Security
Swarm Learning operates on the premise of decentralized and secure machine learning. It's crucial to uphold the highest standards of security to maintain the integrity and confidentiality of your data. Here are the key security aspects to consider while leveraging the power of Swarm Learning:
1. Raw Data Stays on Devices:
In Swarm Learning, raw data remains decentralized on individual devices, ensuring data privacy and limiting access to authorized participants only.
2. Peer-to-Peer Device Connectivity:
Devices are connected peer-to-peer, establishing a collaborative learning environment. This approach enhances privacy by minimizing centralized data repositories.
3. Encrypted VPN Network:
The connection between devices is encrypted via a Virtual Private Network (VPN), adding an extra layer of security to data transmission, making it more resistant to unauthorized access.
4. Certificate-based Participant Verification:
Only participants who have been pre-verified using certificates can actively participate in the Swarm Learning process. This stringent verification process ensures that only authenticated and authorized individuals are part of the training process.
VPN Structure
VPN overview
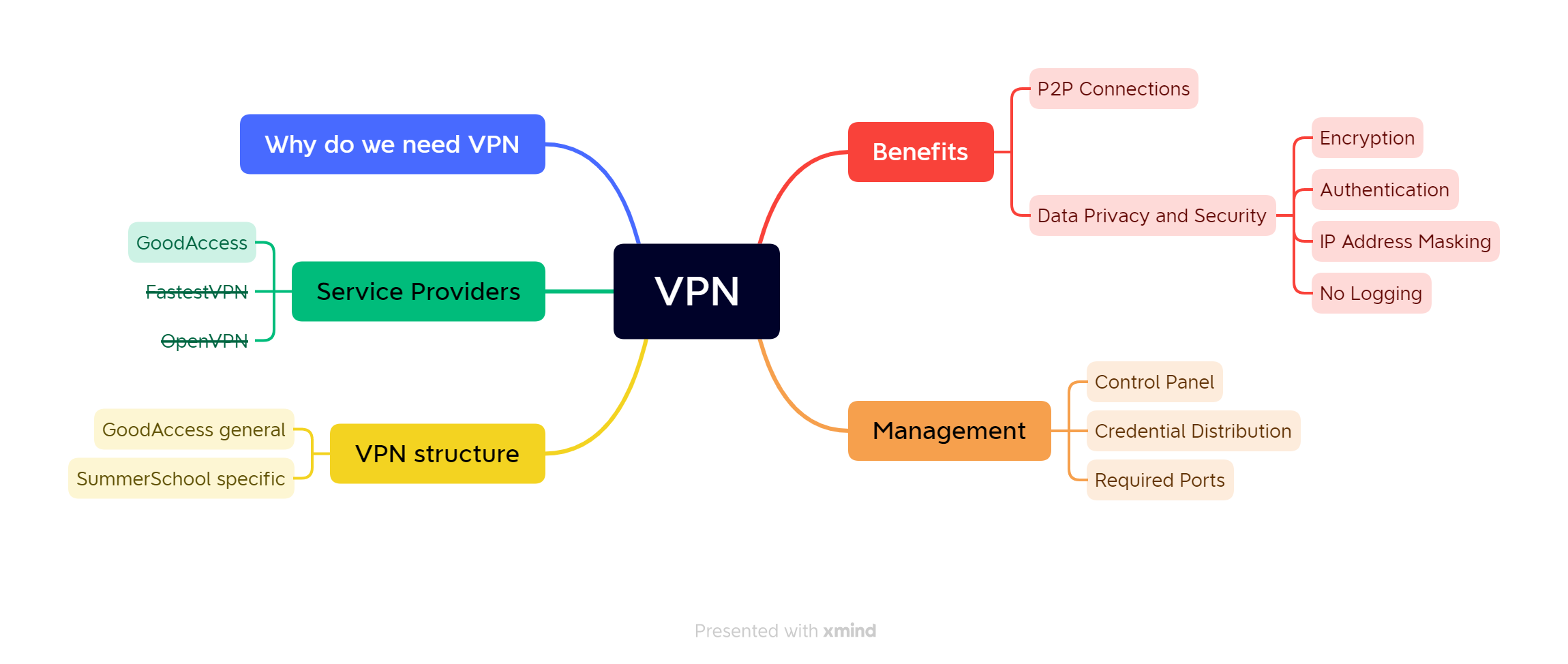
VPN general structure
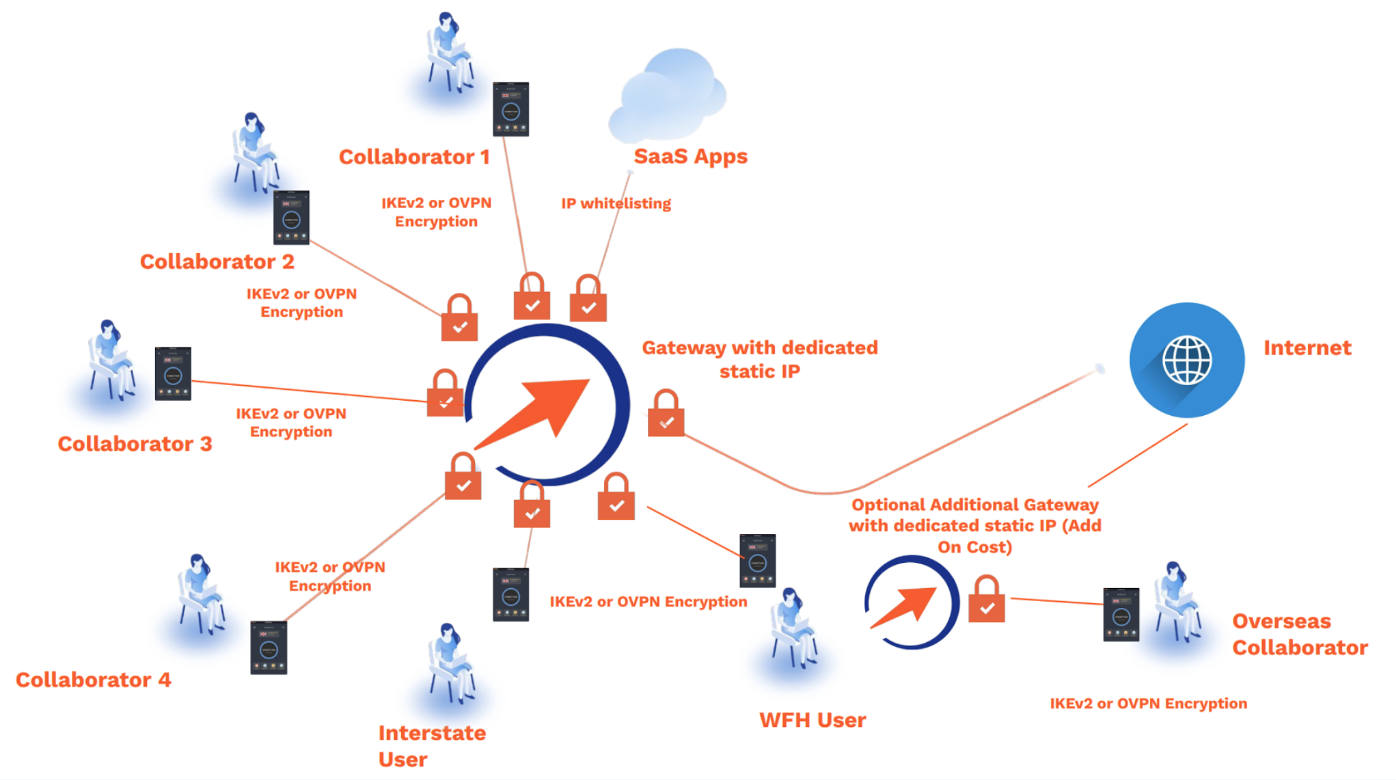
Info
Detailed guidelines and further insights into security practices with Swarm Learning, will follow.
Bugs and Problems
Did you find a bug in the code or other problems? Then raise an issue in our Github repository: https://github.com/KatherLab/swarm-learning-hpe/issues
In case of problems or requests for improvement of the documentation, please raise an issue at: https://github.com/odelia-ai/odelia-ai.github.io/issues